Build Your Cybersecurity Defense Plan: OWASP TaSM Framework (Workshop)
Most cybersecurity teams are drowning in threat intelligence information but struggle to answer one fundamental question:
“What are the 5-7 threats that could actually destroy our business, and what’s our plan to stop them?”
Join the Virtual Workshop:
When: Tuesday, Mar 31st 12:30 PM (Afternoon) - Pacific Standard Time (PST)
Where: Online, via Zoom
🎉 Cybersecurity Club members get FREE access!
The workshop is free for Cybersecurity Club members, or $20 for non-members.
👉 Get a FREE Ticket (usually $20):
https://www.eventbrite.com/e/1981916887763/?discount=CybersecurityClub
🛡️ Not a Cybersecurity Club member yet? Join here! (It’s FREE)
Learn from an Experienced CISO
Learn directly from Ross Young, creator of the OWASP Threat and Safeguard Matrix (TaSM), who developed this framework after 20 years of tackling this exact challenge across some of the most demanding security environments in the world.
From protecting classified operations at the NSA and CIA to serving as CISO at Johns Hopkins University and leading security at Capital One, Ross has repeatedly seen organizations waste resources on low-priority risks while leaving critical threats unaddressed.
The TaSM framework was born from this experience: a clear, actionable approach that helps you focus resources on the threats that actually threaten YOUR business, then build a comprehensive defense-in-depth strategy that executives can understand.
Rather than trying to “fill every box” in traditional security frameworks, TaSM starts with your material threats and works backward to the safeguards that matter most.
In this workshop, Ross (currently host of the CISO Tradecraft podcast and author of “Cybersecurity’s Dirty Secret”) will guide you through building your own Threat and Safeguard Matrix.
You’ll gain the same strategic thinking approach used to protect national security assets, Fortune 500 companies, and critical infrastructure, adapted for your organization’s specific threat landscape.
This is your opportunity to learn a battle-tested framework directly from the security leader who created it, refined it across government and industry, and now shares it as an open-source OWASP project to help security teams worldwide stop wasting budget and start defending what actually matters.
What You’ll Learn
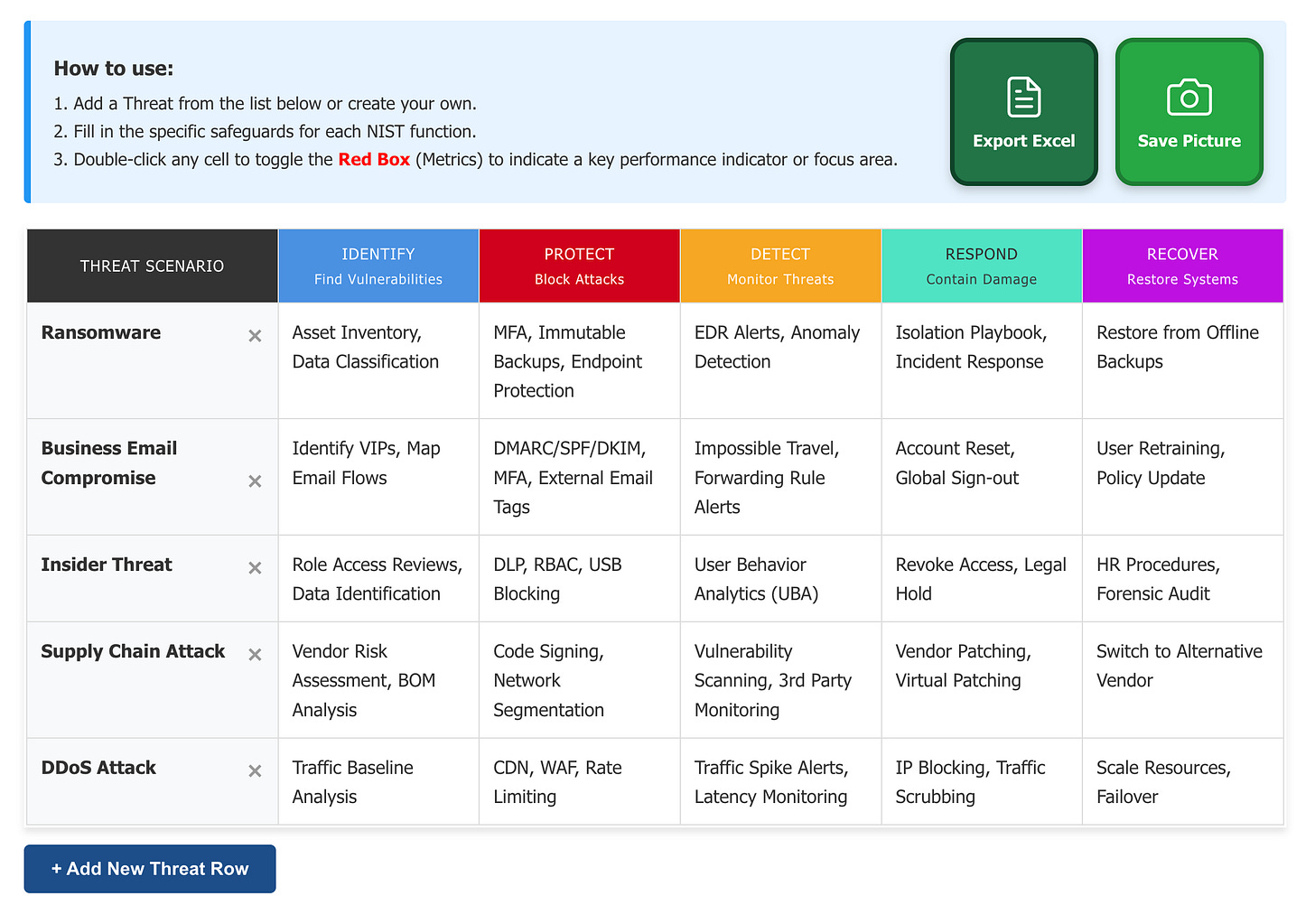
This interactive workshop guides you through building your own Threat and Safeguard Matrix from scratch:
1. Identify Your Material Threats
Start by cataloging the threats that pose real risk to your organization (not theoretical vulnerabilities, but actual attack vectors that could cause business disruption, financial loss, or reputational damage). Examples include:
Business Email Compromise and phishing campaigns
Ransomware attacks targeting critical systems
Web application vulnerabilities (SQL injection, XSS, authentication bypass)
Third-party vendor data breaches
Supply chain compromises (malicious open-source libraries, hardware implants)
Insider threats and privilege abuse
Cloud misconfigurations exposing sensitive data
DDoS attacks disrupting operations
2. Map Defenses Across the NIST Cybersecurity Framework
For each material threat, you’ll identify safeguards across all five NIST CSF functions:
Identify: Vulnerability scanning, asset management, risk assessments, penetration testing
Protect: EDR/antivirus, email security gateways, web application firewalls (WAF), access controls, MFA, security awareness training
Detect: SIEM, intrusion detection systems (IDS), deception technology, user behavior analytics, threat intelligence
Respond: Incident response playbooks, forensics tools, containment procedures, communication plans
Recover: Backup and disaster recovery systems, business continuity plans, post-incident reviews
3. Build Measurable Security Metrics
Transform your TaSM into an executive-friendly scorecard with:
Status: Where are you now? (e.g., Mean Time to Remediate vulnerabilities = 60 days)
Trends: Are you improving or declining? (visual trend lines)
Goals: Where do you want to be? (target MTTR = 30 days)
Due Dates: When will you achieve your goals?
These metrics help you tell a compelling story to leadership: “We’ve reduced phishing click rates from 33% to 20% this quarter” or “100% of critical applications now have tested backup recovery procedures to defend against ransomware.”
4. Justify Security Budgets
Connect every dollar spent to specific threats and business outcomes. Instead of “We need $200K for EDR,” you can say: “This $200K EDR investment is a critical component of our ransomware defense strategy, which protects $50M in annual revenue from operational disruption.”
Interactive Workshop: AI Security Threats
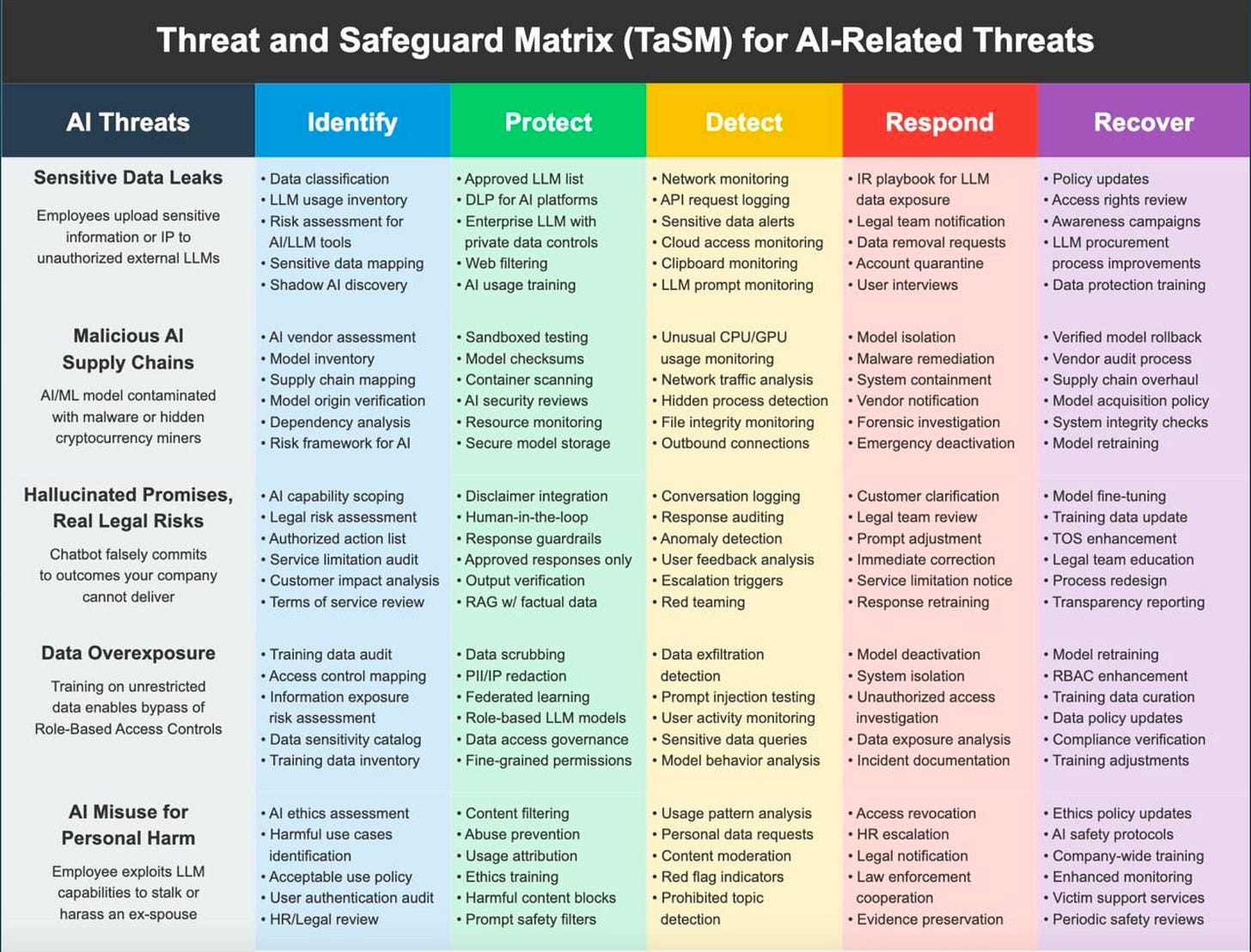
You’ll apply the TaSM framework to real-world generative AI and LLM security challenges:
Sensitive Data Leaks: Employees uploading proprietary information to external AI tools
Malicious AI Supply Chains: Contaminated ML models with embedded malware or crypto miners
Hallucination Liability: AI chatbots making commitments your company can’t deliver
Data Overexposure: Training data that bypasses role-based access controls
AI Misuse: Employees exploiting LLM capabilities for harassment or stalking
You’ll leave the workshop with a completed AI threat matrix you can immediately adapt for your organization.
What Makes TaSM Different
Solves the “Security Bingo” Problem
Traditional frameworks like NIST CSF include 108+ safeguards, CIS Controls lists 153 implementation guidelines. Teams feel pressured to implement everything, leading to:
Scattered resources across too many initiatives
Difficulty explaining strategy to executives
Wasted budget on solutions that don’t address real threats
No clear measure of progress
TaSM flips this approach: start with YOUR threats, then implement only the safeguards that defend against those specific risks.
Executive Communication
Non-technical leaders understand business threats (ransomware, data breaches, vendor compromises) far better than technical jargon (CVEs, CVSS scores, EDR telemetry). TaSM bridges this gap by organizing security activities around business risks.
Defense in Depth, Visualized
See how your entire security stack works together. For example, your phishing defenses might include:
Identify: Security awareness training, phishing simulations
Protect: Email security gateway, MFA, DNS filtering
Detect: User reporting mechanisms, deception technology, SIEM alerts
Respond: Incident response playbooks, account quarantine procedures
Recover: Post-incident training, blameless post-mortems
Scalable and Adaptable
TaSM works for organizations of any size and can extend beyond cybersecurity to enterprise risk management. Map threats from Compliance (anti-money laundering), Finance (interest rate changes), HR (employee health), and Legal (regulatory changes) all in one unified framework.
What You’ll Take Home
✅ Cyber Inventory Template: Google Sheets template with common security technologies
✅ Interactive TaSM Tool: Web-based tool to build and visualize your matrix
✅ Workshop Exercise: Completed AI threat matrix via collaborative Miro board
✅ Metrics Dashboard Examples: Real scorecards showing vulnerability management, patching compliance, phishing metrics, disaster recovery testing
✅ Threat Modeling Integration: How to use TaSM with STRIDE-LM for application security reviews
✅ Budget Justification Framework: Connect spending to material threats and business outcomes
About the Instructor: Ross Young, Creator of the OWASP TaSM Framework
Ross Young created the OWASP Threat and Safeguard Matrix (TaSM) to solve a problem he encountered repeatedly throughout his 20-year cybersecurity career: security teams struggling to explain their strategy to executives and justify budget decisions in terms of actual business risk.
As founder of CISO Tradecraft and the architect of the TaSM framework, Ross has refined this approach across diverse environments in education, commercial industry, and government:
Education Sector:
Johns Hopkins University (CISO role)
Commercial Industry:
Capital One (financial services security)
CAT Financial (industrial security)
Team8 (cybersecurity innovation)
Government:
National Security Agency (NSA)
Central Intelligence Agency (CIA)
Federal Reserve Board of Governors
Ross is the author of “Cybersecurity’s Dirty Secret: Why Most Budgets Go to Waste,”. His work on TaSM has been recognized as an OWASP Incubator Project and is used by security teams worldwide to prioritize defenses and communicate risk effectively.
He hosts the CISO Tradecraft podcast and has led security programs protecting everything from classified government operations to billion-dollar financial transactions. His approach emphasizes practical, measurable security that focuses on defending against material threats rather than checking compliance boxes.
Who Should Attend
Chief Information Security Officers (CISOs) and security directors
Security architects and engineers
Risk management professionals
IT directors and managers
Compliance officers (PCI DSS, HIPAA, SOC 2, ISO 27001)
Anyone responsible for communicating security strategy to executives
Teams building or improving their security programs
Cybersecurity students, learners and enthusiasts
No prior knowledge of NIST CSF or OWASP frameworks required (just bring your organization’s security challenges).
Session Details
Format: Interactive workshop with lecture, discussion, and exercises.
Date: Tuesday, March 31, 2026
Time: 12:30-1:30pm Pacific Time (Los Angeles)
Join Us
Transform your security program from reactive and scattered to strategic and measurable. Stop solving problems you don’t have. Start defending against threats that actually matter.
When: Tuesday, Mar 31st 12:30 PM (Afternoon) - Pacific Standard Time (PST)
Where: Online, via Zoom
Learn the TaSM framework directly from its creator and discover why organizations worldwide are adopting this approach to focus their cybersecurity resources where they’ll have the greatest business impact.
🎉 Cybersecurity Club members get FREE access!
The workshop is free for Cybersecurity Club members, or $20 for non-members.
👉 Get a FREE Ticket (usually $20): https://www.eventbrite.com/e/1981916887763/?discount=CybersecurityClub
🛡️ Not a Cybersecurity Club member yet? Join here! (It’s FREE)